-
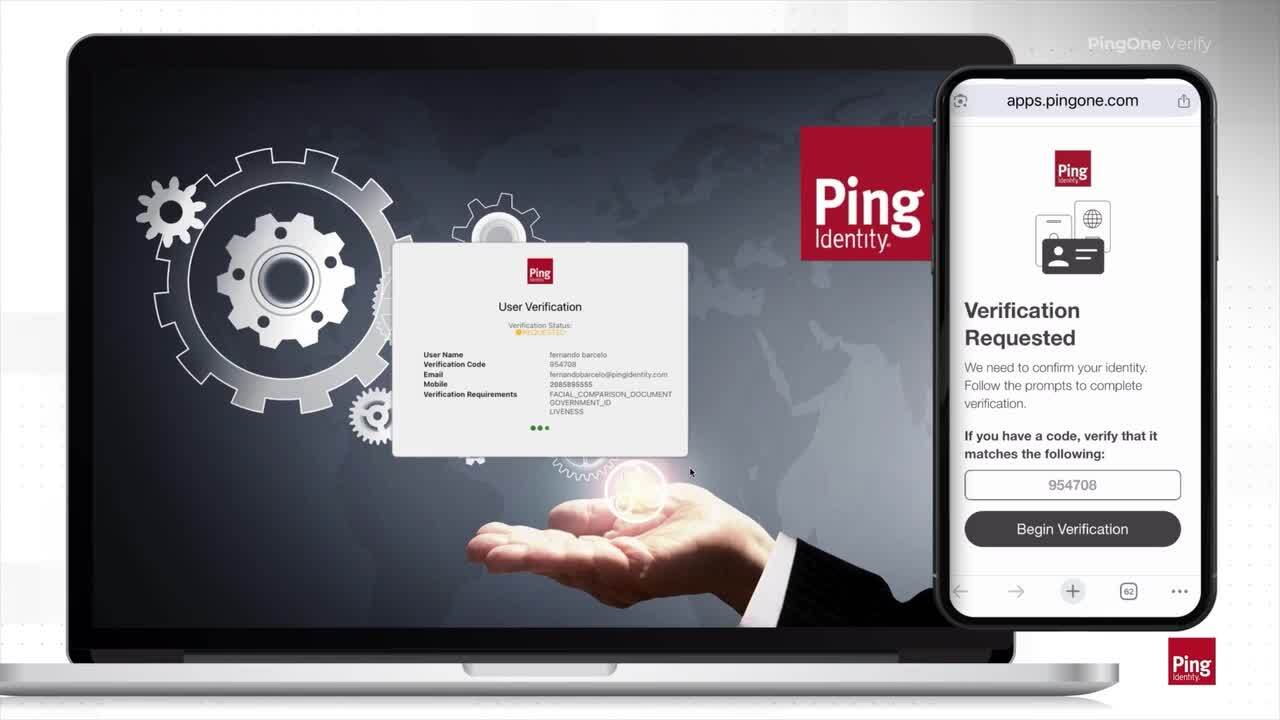
Stop Helpdesk Attacks before they Start with PingOne Verify
Social engineering attacks on helpdesks are growing. See how PingOne Verify stops them with fast, secure ID confirmation using AI, biometrics, and real-time monitoring.
2:27
-
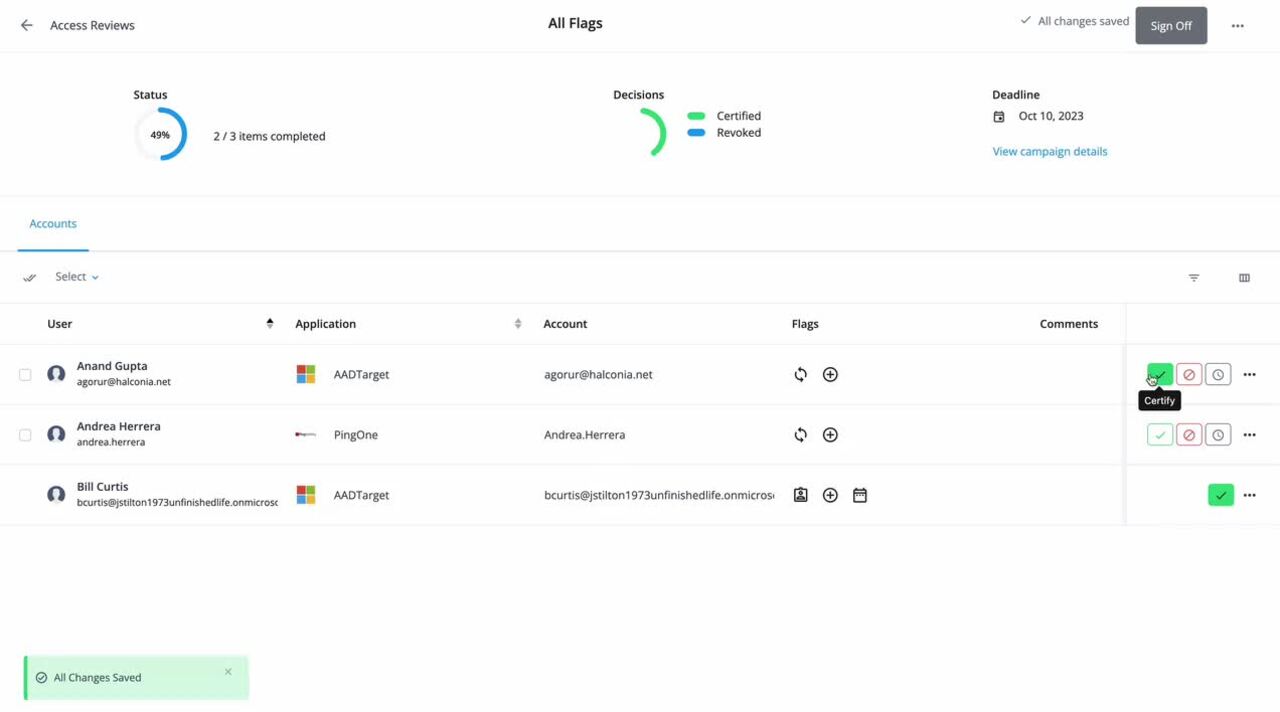
Identity Governance End User Certification Steps
How end users can create an access request to gain access to resources (applications, entitlements, or roles). They can request access for themselves or on behalf of others.
0:32
-
Identity Governance Access Requests Create Request
How end users can create an access request to gain access to resources (applications, entitlements, or roles). They can request access for themselves or on behalf of others.
1:44
-
Workforce IAM
Say hello to the new ForgeRock Identity governance. A cloud native governance solution designed to help solve security and compliance challenges for large enterprises at scale.
2:01
-
Identity Live 2020 Virtual Edition Highlights
Learn about the latest release of the ForgeRock Identity platform that includes our new Autonomous Identity product, an AI driven identity analytics solution that applies unmatched AI driven intelligence to identity management and governance.
5:40
-
A Trusted Partner for Government Agencies
Support your agency’s distributed workforce to perform interoperable mission work while keeping up with the rapidly transforming threat landscape. Ping’s government identity solutions have you covered.
1:58
-
Identity Is The Core Of Zero Trust
Hear from Richard Bird, CCIO at Ping Identity, as he discusses the current state of identity in the Federal Government, why Zero Trust is dependent upon identity, and how building upon existing ICAM programs supports the move to Zero Trust.
18:26
-
Curbing the Flow of Ransomware: Real or Pipe Dream
Industry experts discuss the state of our nation’s cybersecurity, the impact of the Biden administration’s cybersecurity executive order and infrastructure plan, and how government and industry can coordinate to protect critical infrastructure.
1:03:47
-
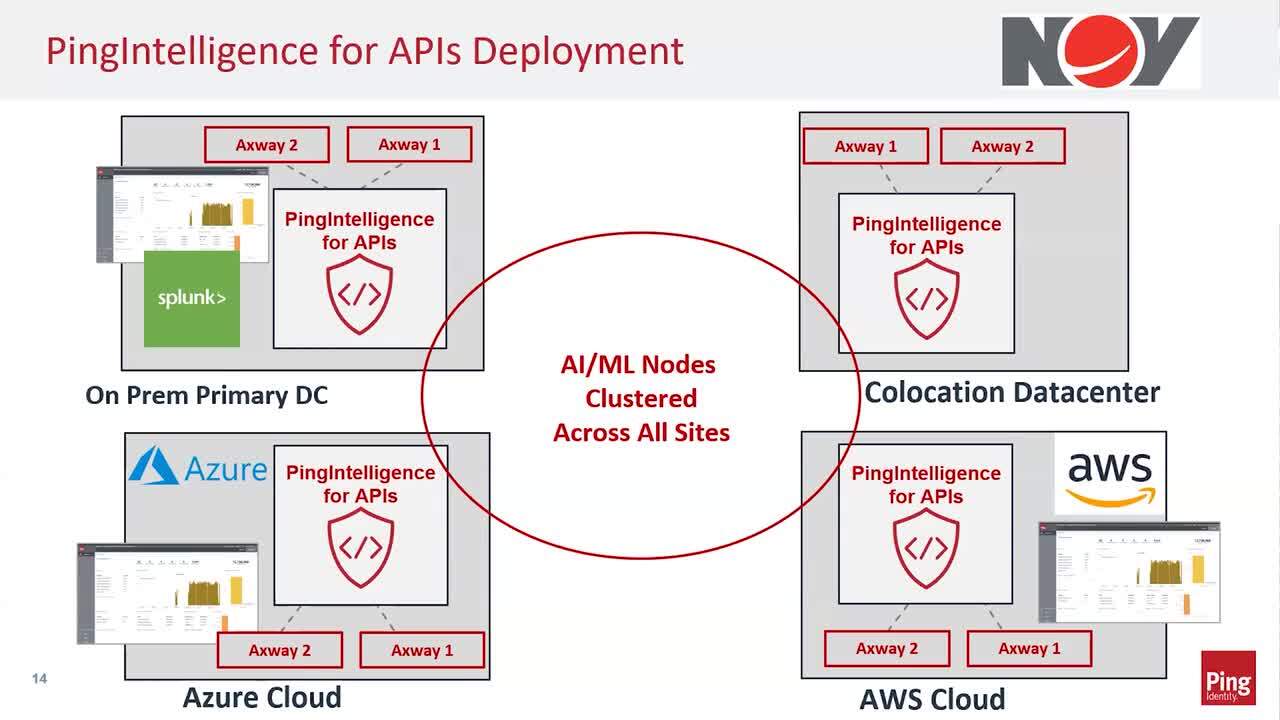
API Infrastructures Risk & Governance with a Layered Security Approach
Learn how to properly secure infrastructures to enable digital transformation and the use of APIs. In this IDENTIFY session, Manoj Kona from National Oilwell Varco shares how NOV has been successful using PingIntelligence for APIs.
20:49
-
SailPoint and Ping Identity
Strengthen your security posture with global identity governance and administration leader SailPoint and identity and access management leader Ping Identity.
2:28
-
Identity Defined Security with the Ping Identity Platform
As the digital enterprise continues to give users unprecedented access to applications and data, it is imperative they move to dynamic and continuous authentication and authorization with data access governance and privacy management.
5:09
-
Governmental Digital Transformation
Richard Bird, Chief Customer Information Officer at Ping Identity speaks about government prioritization of new Digital Identity initiatives.
2:53