-
Use Case - Provision users to and from Identity Cloud and PingDirectory
A use case detailing how to provision data to and from Identity Cloud and a PingDirectory server.
1:17
-
Use Case - Customize Theme
A use case detailing how an administrator can customize the look and feel and the what items an end user has access to view.
0:42
-
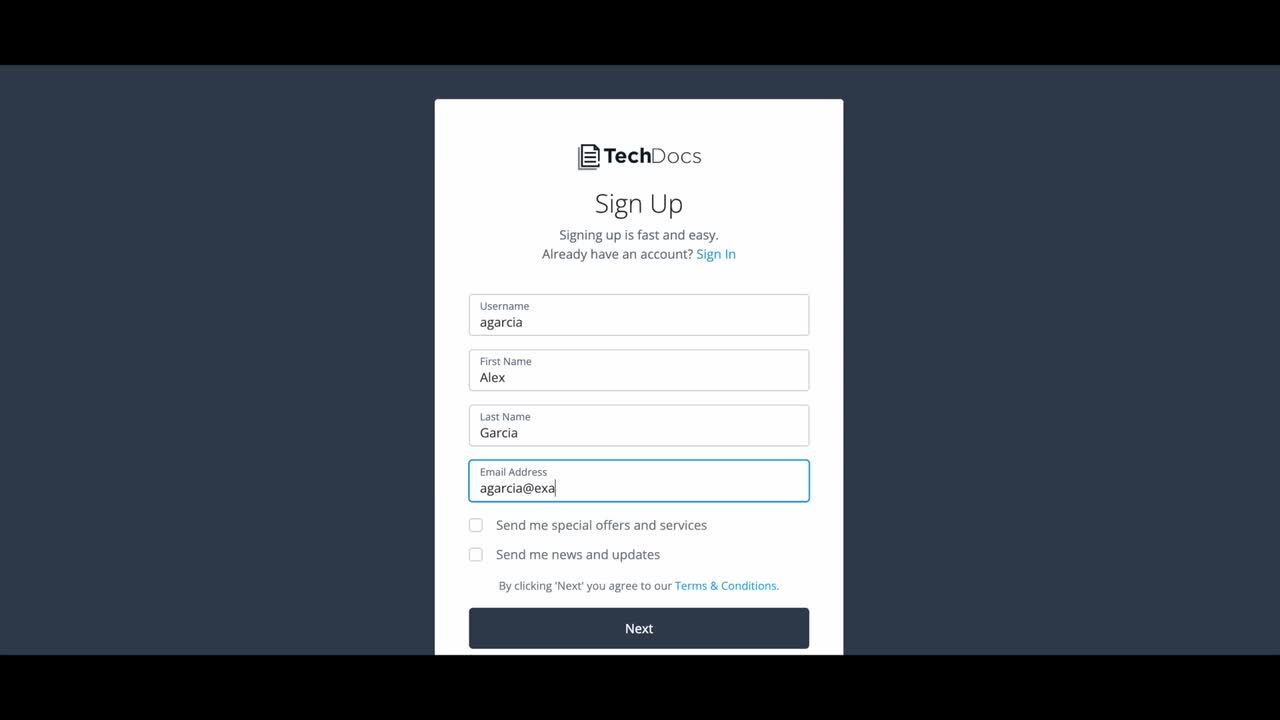
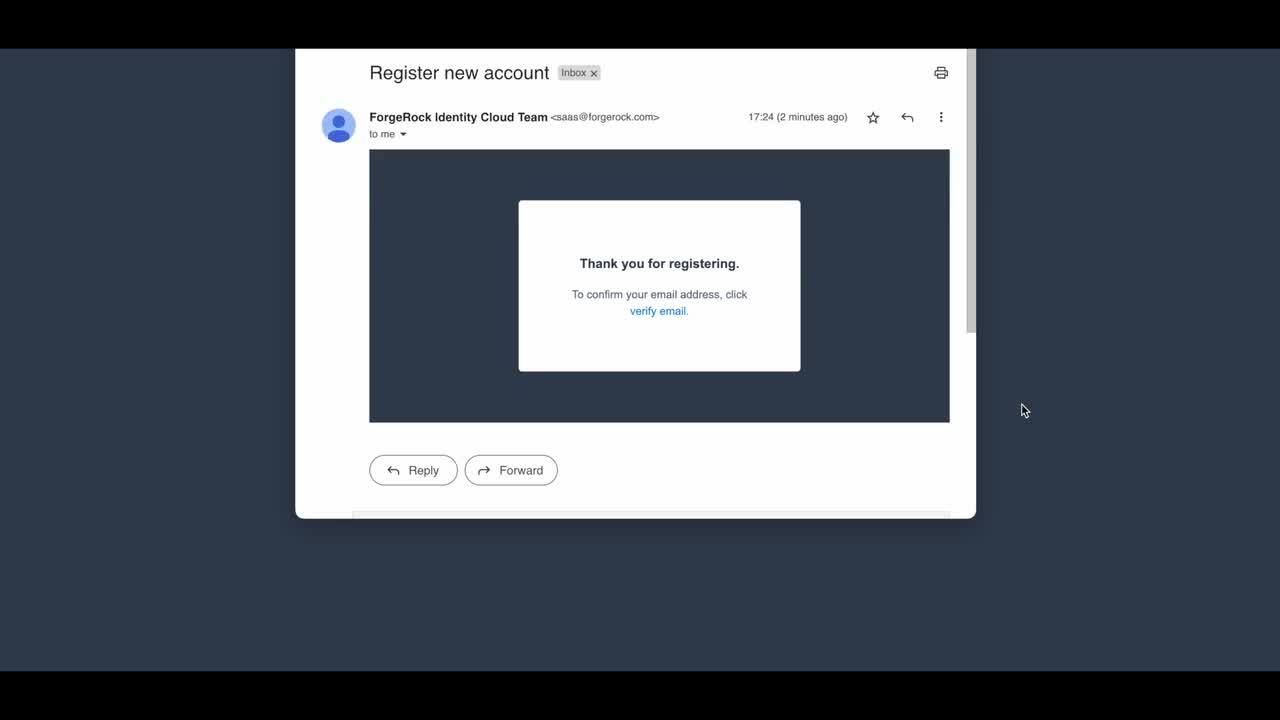
Use Case - User Registration
A use case detailing how to create a journey in Identity Cloud for user registration.
0:47
-
Use Case - Customize Email
A use case detailing how an administrator can customize emails in Identity Cloud.
0:31
-
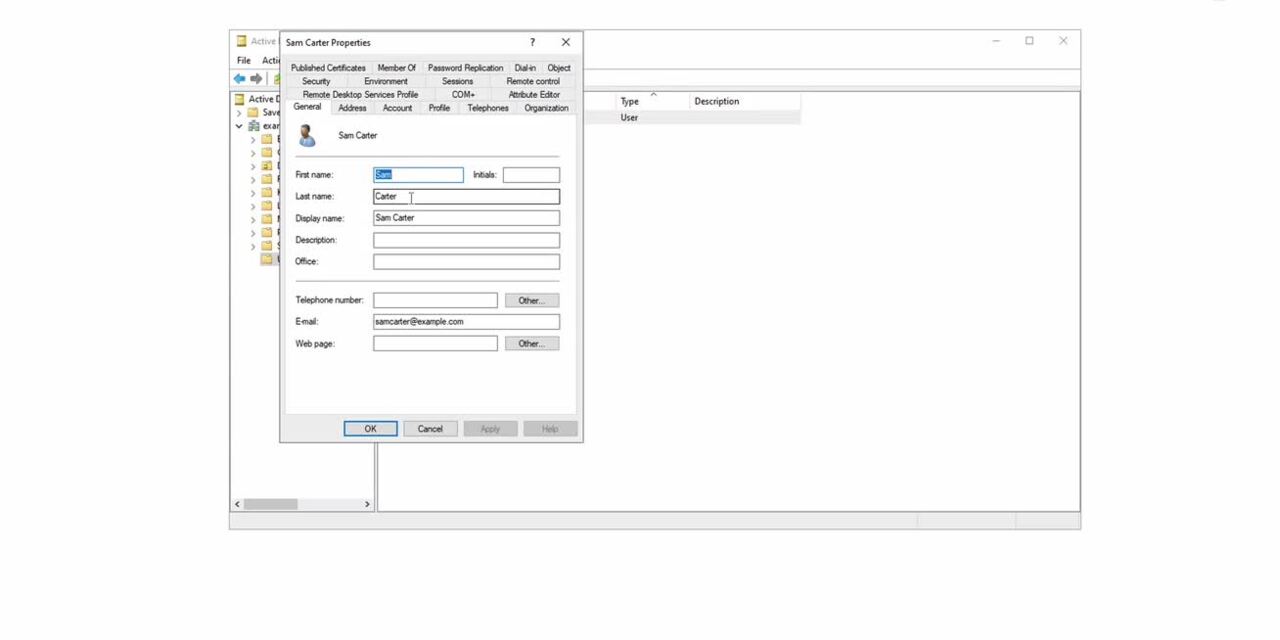
Use Case - Sync from on-prem data store using RCS (AD)
A use case detailing how to sync users from an on-premise data source into Identity Cloud. This uses Identity Cloud's remote connector server (RCS), which is deployed on-premise to connect an organization's intranet with Identity Cloud. In this case,
1:03
-
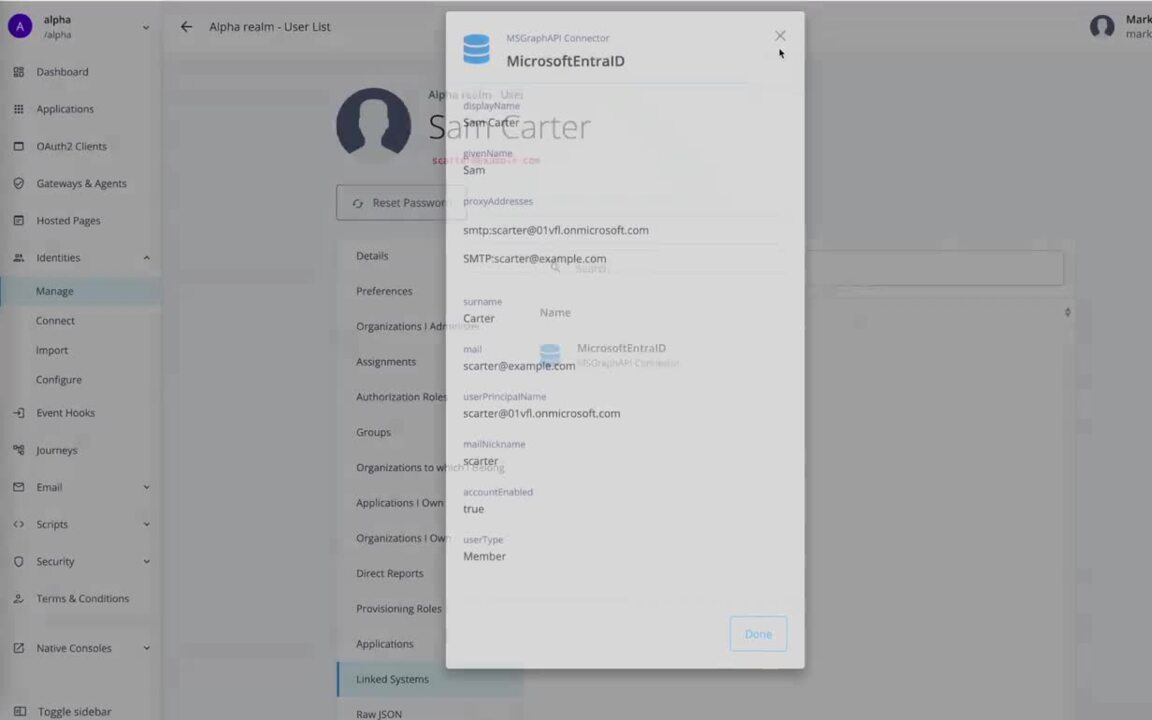
Use Case - Provision from cloud-based application (Microsoft Entra ID)
A use case detailing how to use Identity Cloud's application templates to quickly provision users from an external data source. In this case, the external data source is Microsoft Entra ID (Azure AD).
1:09
-
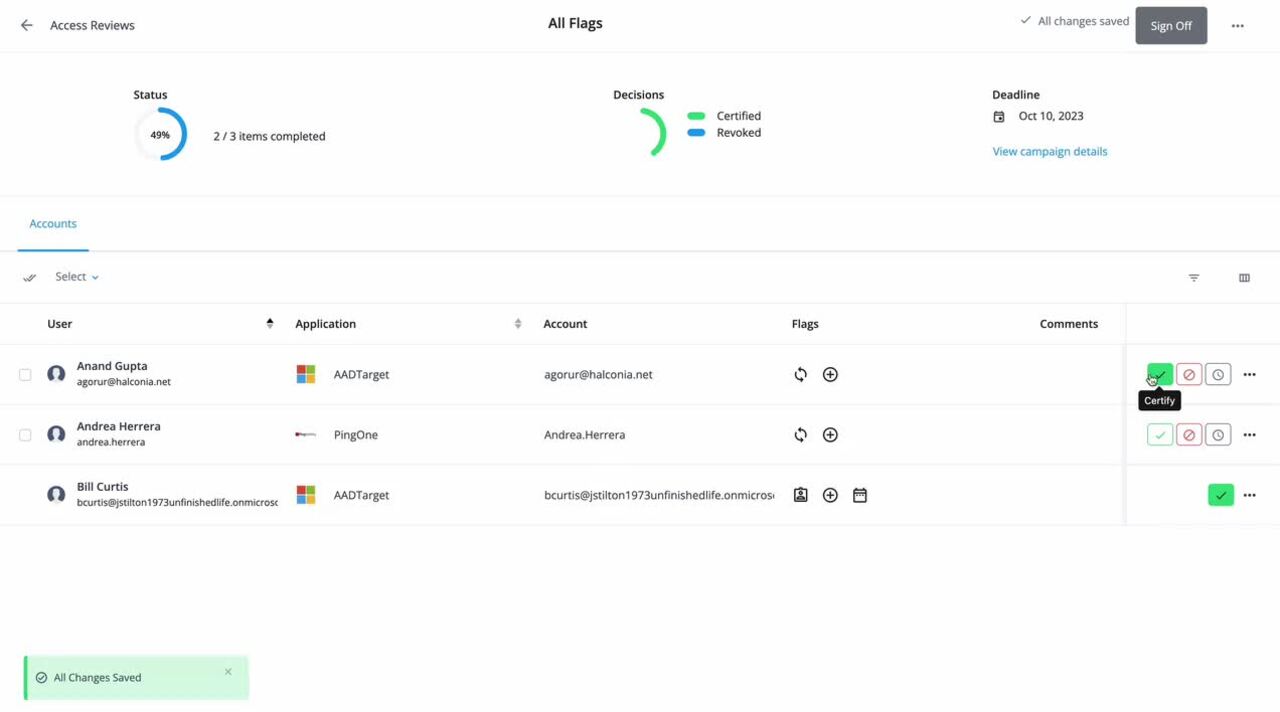
Identity Governance End User Certification Steps
How end users can create an access request to gain access to resources (applications, entitlements, or roles). They can request access for themselves or on behalf of others.
0:32
-
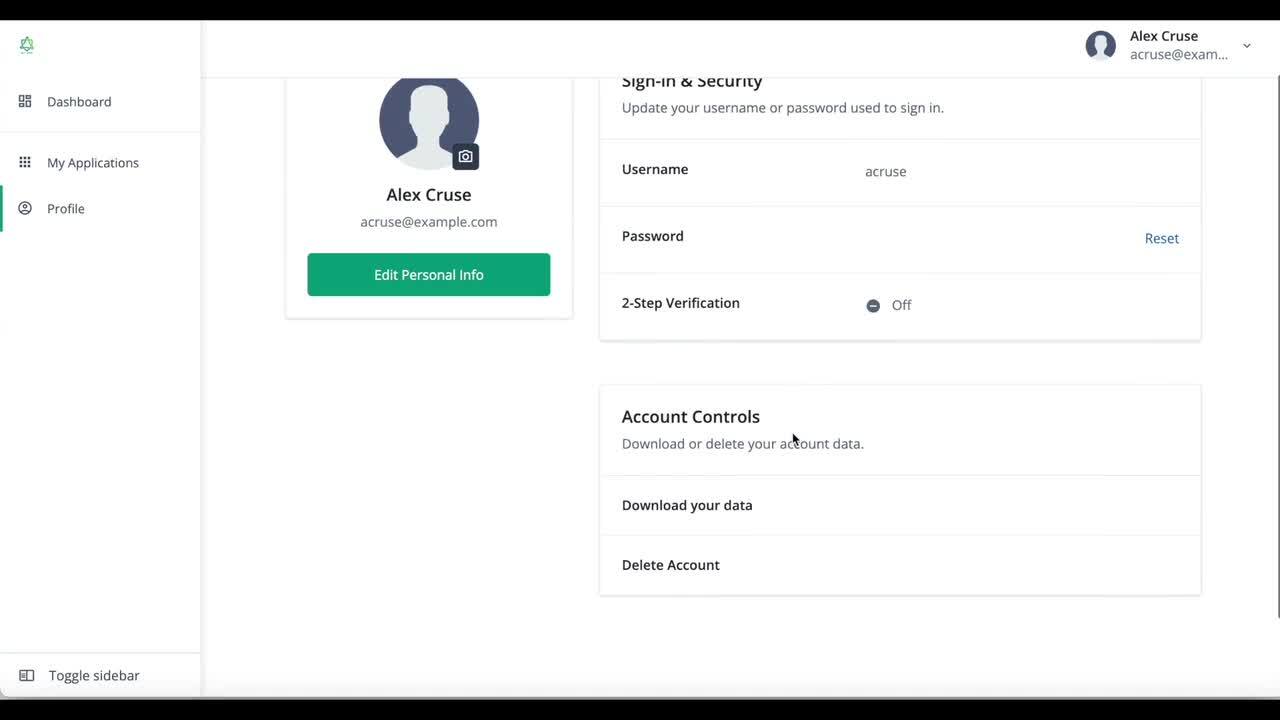
End user my apps dashboard
A short video showing an end user can view applications they have access to in the Identity Cloud end-user UI.
0:50
-
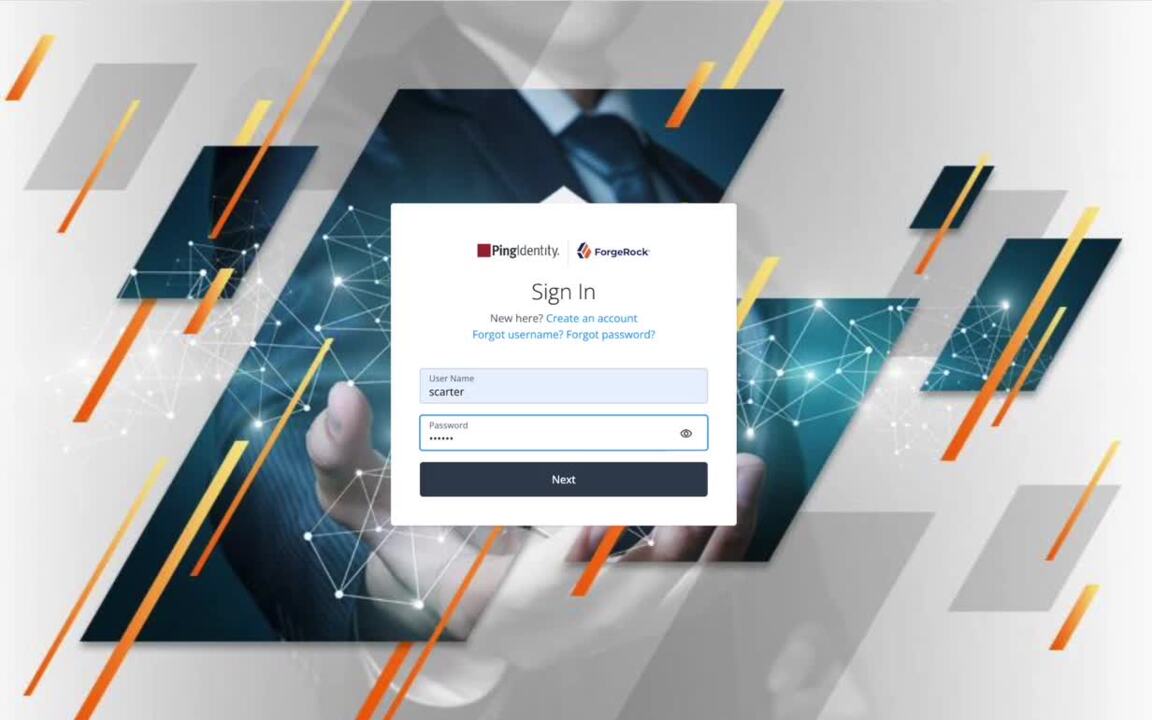
Use Case - Login with MFA using push notifications
A use case detailing how an end user can login to Identity Cloud and be prompted to perform push MFA using the ForgeRock Authenticator application.
0:41
-
Disable user properties from end user
A short video detailing how an administrator can disable attributes shown to end users. By default, Identity Cloud enables all properties.
0:36
-
Use Case - Create a script in a journey to record last login time
A use case detailing how to write a script in a journey. In this case, how to record the last successful login time for and end user, and store the time in their profile.
0:32
-
Identity Governance Access Requests Create Request
How end users can create an access request to gain access to resources (applications, entitlements, or roles). They can request access for themselves or on behalf of others.
1:44
- Load More