Why Now Is the Time for Zero Trust
14:42
As a remote workforce becomes the norm, the need for Zero Trust has never been greater.
Related Videos
In Workforce Identity
-
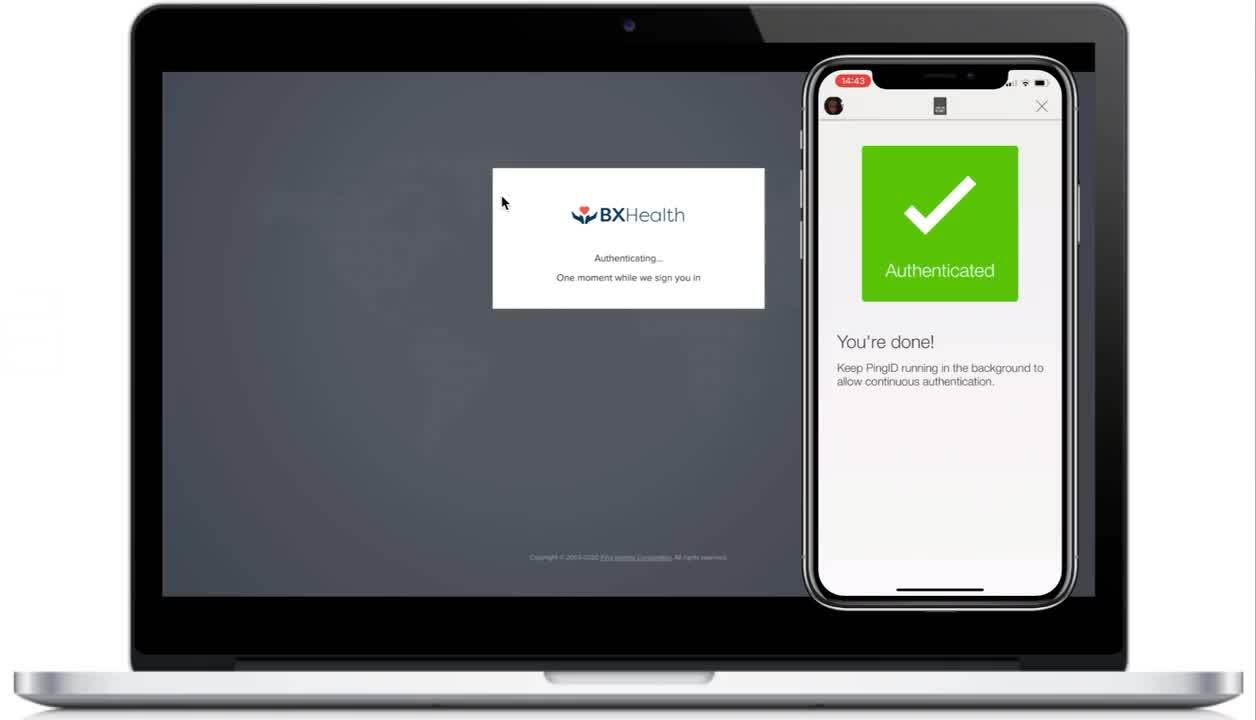
Play video Healthcare Workforce Demo
Healthcare Workforce Demo
This demonstration walks through a day in the life of a healthcare employee. Watch to see how single sign-on, MFA, self-service, medium and fine-grained authorization and more help make BXHealth employees more productive and secure.
4:00
-
Play video Break the IT Slow-down Cycle
Break the IT Slow-down Cycle
Experience how a workforce authentication authority can free you from productivity roadblocks and free you from the vicious cycle of too many requests, too many passwords and not enough hours in the day. Learn more at pingidentity.com/workforceguide
1:59
-
Play video Retail Workforce Demo
Retail Workforce Demo
This demonstration walks through a day in the life of a retail employee. See how single sign-on, MFA, self-service, medium and fine-grained authorization and more help make BXRetail employees more productive and secure.
4:01
-
Play video Workforce Identity Value Calculator
Workforce Identity Value Calculator
Workforce identity keeps your organization secure, productive and agile. Without it, your digital transformation is doomed. Our calculator can help IT professionals quantify and communicate the true business value of workforce identity investments.
2:19
-
Play video Identity Is The Core Of Zero Trust
Identity Is The Core Of Zero Trust
Hear from Richard Bird, CCIO at Ping Identity, as he discusses the current state of identity in the Federal Government, why Zero Trust is dependent upon identity, and how building upon existing ICAM programs supports the move to Zero Trust.
18:26
-
Play video Manufacturing Workforce Demo
Manufacturing Workforce Demo
This demonstration walks through a day in the life of a manufacturing employee. Watch to see how single sign-on, MFA, self-service, medium and fine-grained authorization and more help make BXManufacturing employees more productive and secure.
4:01