Identity Defined Customer Engagement with the Ping Identity Platform
4:58
Enterprises must meet requirements to ensure secure, seamless access across engagement channels.
Related Videos
In Web/API Access
-
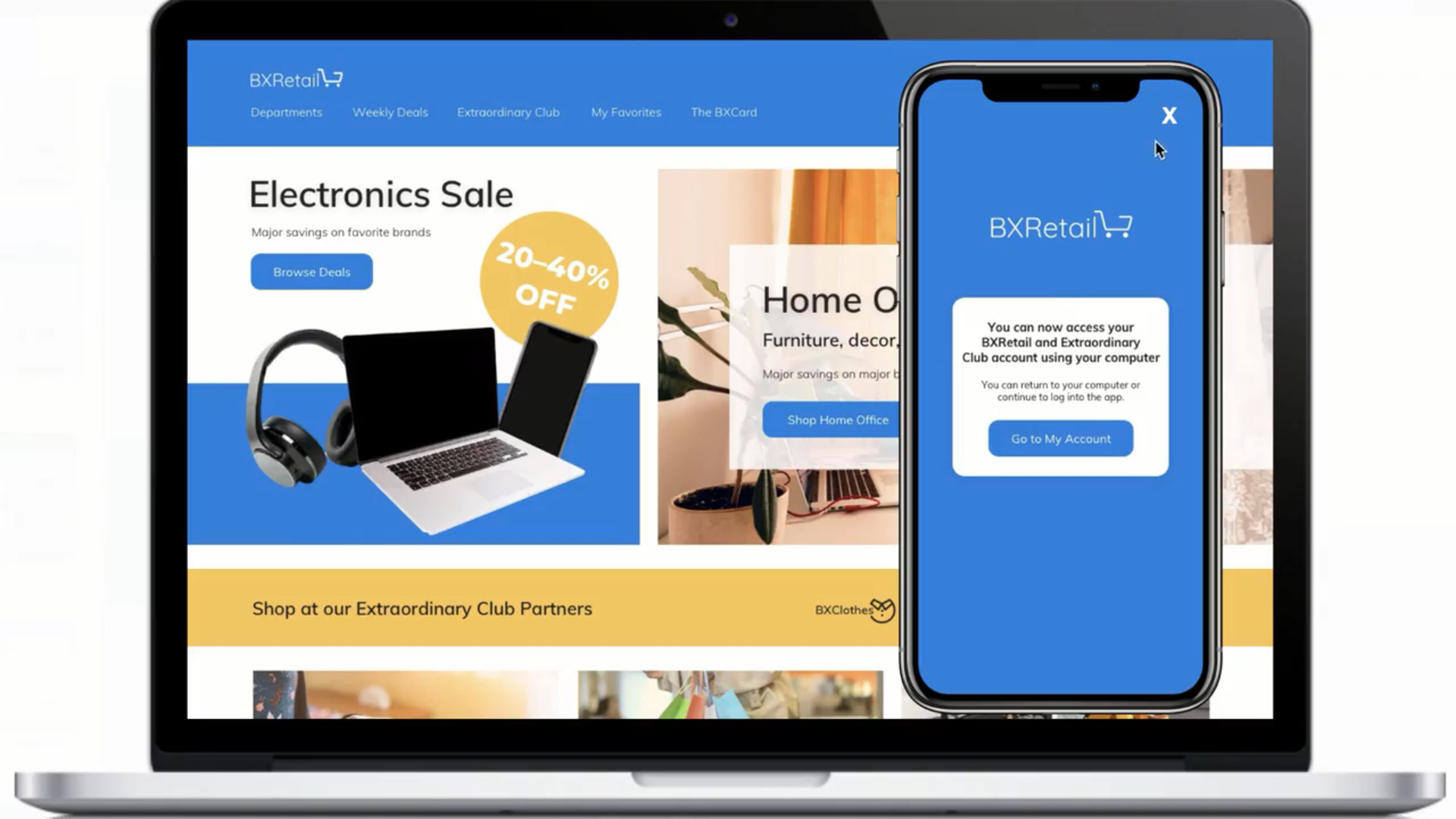
Play video Retail User Journey Demo
Retail User Journey Demo
Online retail customers have high expectations when it comes to personalized, seamless and secure experiences. Explore 5 use cases demonstrating how the Ping Identity Platform can help retailers deliver experiences that will wow their customers.
7:00
-
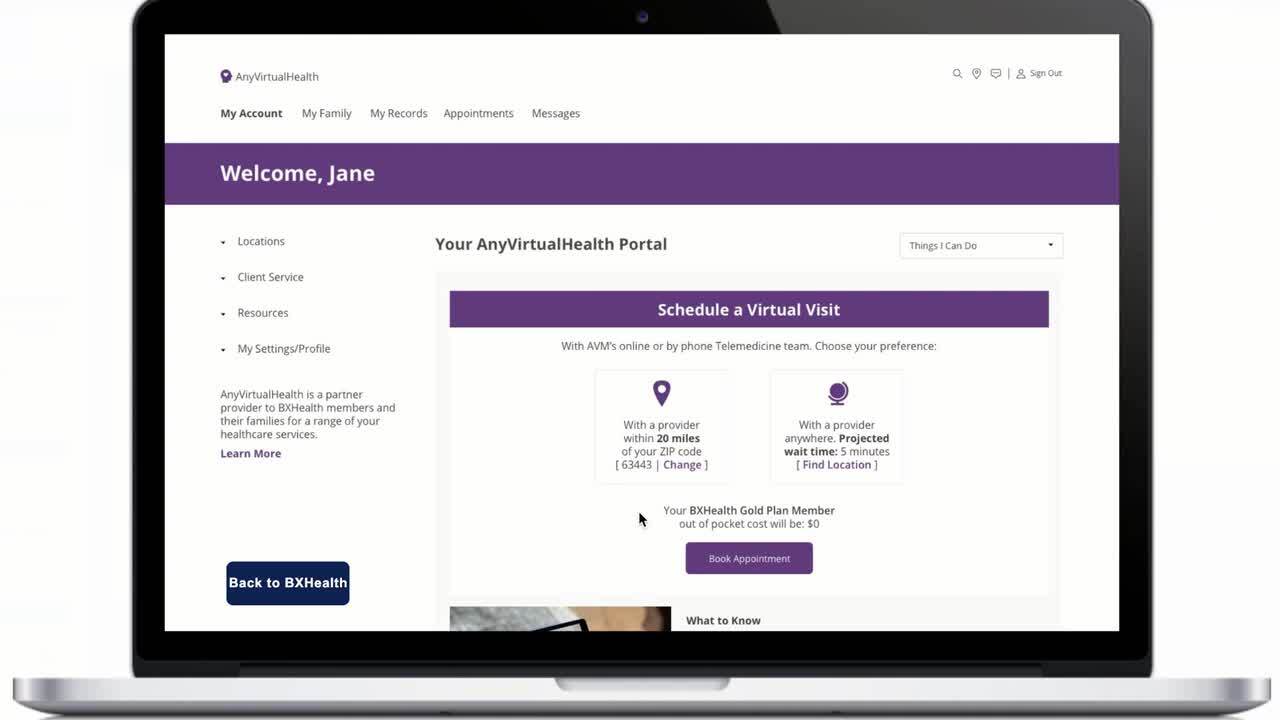
Play video Healthcare User Journey Demo
Healthcare User Journey Demo
Give online health members and patients personalized, seamless and secure experiences with the Ping Identity Platform. This demo will explore 5 use cases, including registration, passwordless login, SSO and consent management.
5:44
-
Play video Identity Defined Security with the Ping Identity Platform
Identity Defined Security with the Ping Identity Platform
As the digital enterprise continues to give users unprecedented access to applications and data, it is imperative they move to dynamic and continuous authentication and authorization with data access governance and privacy management.
5:09
-
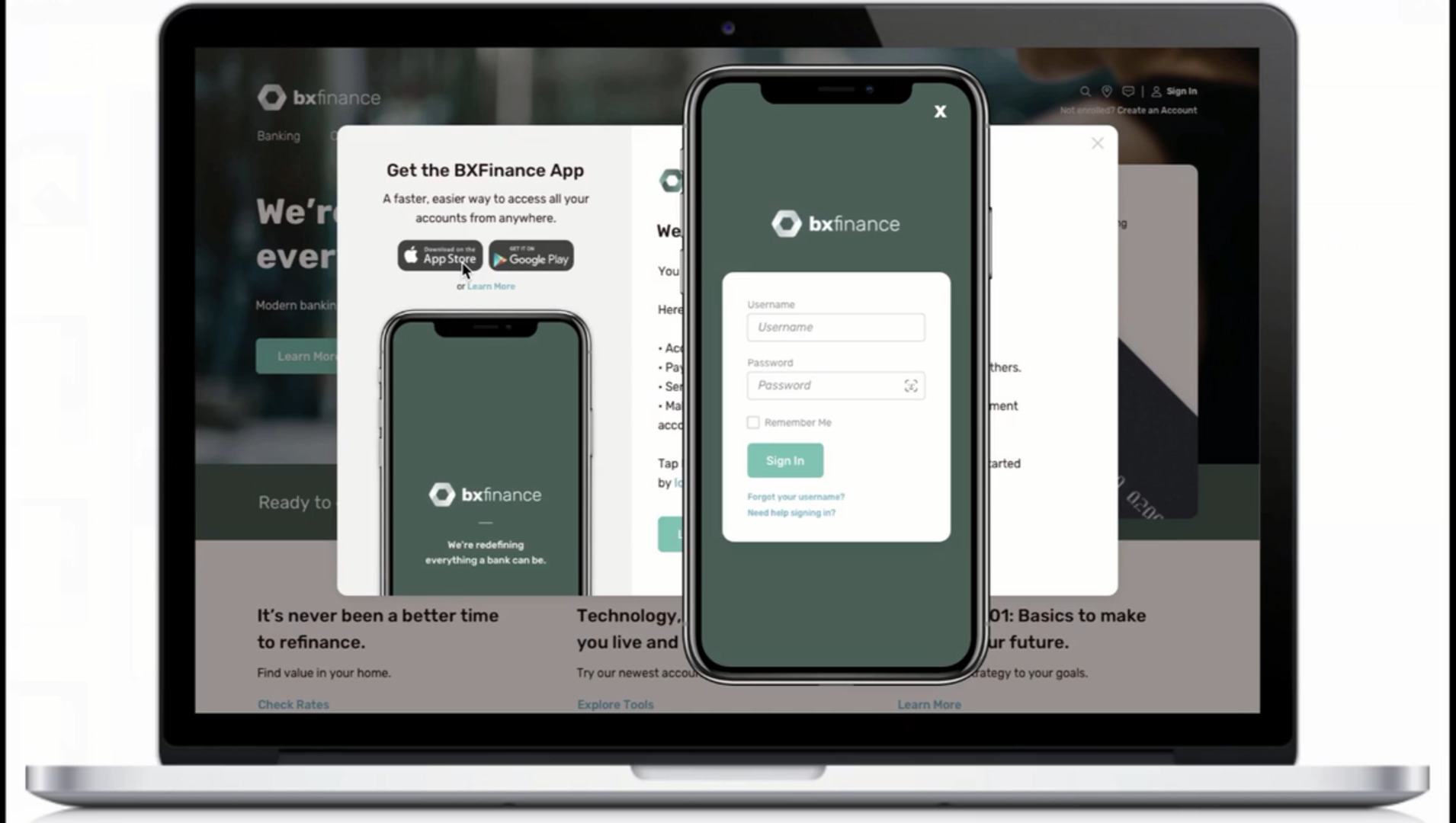
Play video Financial Services User Journey Demo
Financial Services User Journey Demo
Online banking customers demand personalized, seamless and secure experiences. Explore 5 use cases demonstrating how the Ping Identity Platform can help you deliver, from registration to transaction approval to consent management.
5:51
-
Play video Manufacturing Workforce Demo
Manufacturing Workforce Demo
This demonstration walks through a day in the life of a manufacturing employee. Watch to see how single sign-on, MFA, self-service, medium and fine-grained authorization and more help make BXManufacturing employees more productive and secure.
4:01
-
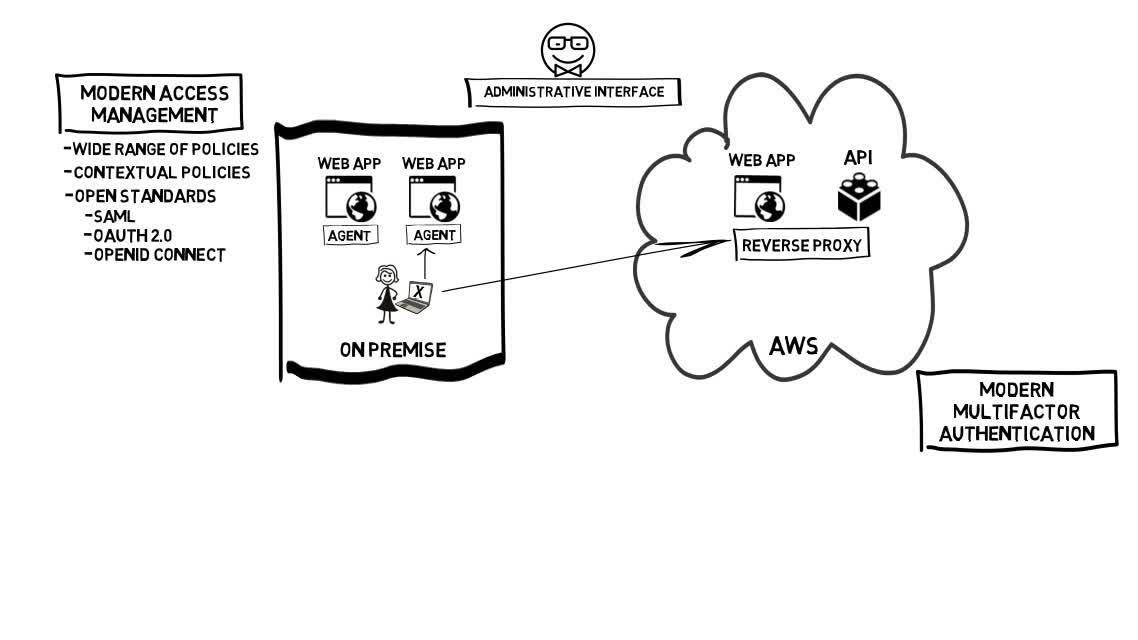
Play video Modernizing Legacy Identity and Access Management Systems
Modernizing Legacy Identity and Access Management Systems
Modern IAM solutions built on open standards provide employees/partners with seamless and secure access anytime, anywhere and enable organizations to lower cost, improve security, and support their new digital business initiatives.
5:21