Introducing the Ping Identity Consumer Data Right Sandbox for Open Banking
2:38
How to use the Ping Identity Consumer Data Right Sandbox for Open Banking
Related Videos
In Regulatory and Compliance
-
Play video Quickstart Private Sandbox for Open Banking & PSD2
Quickstart Private Sandbox for Open Banking & PSD2
Our Quickstart Private Sandbox helps banks accelerate the deployment of an environment that conforms with Open Banking and PSD2. This video demonstrates the script being installed and walks you through two use cases for payments and account APIs.
2:23
-
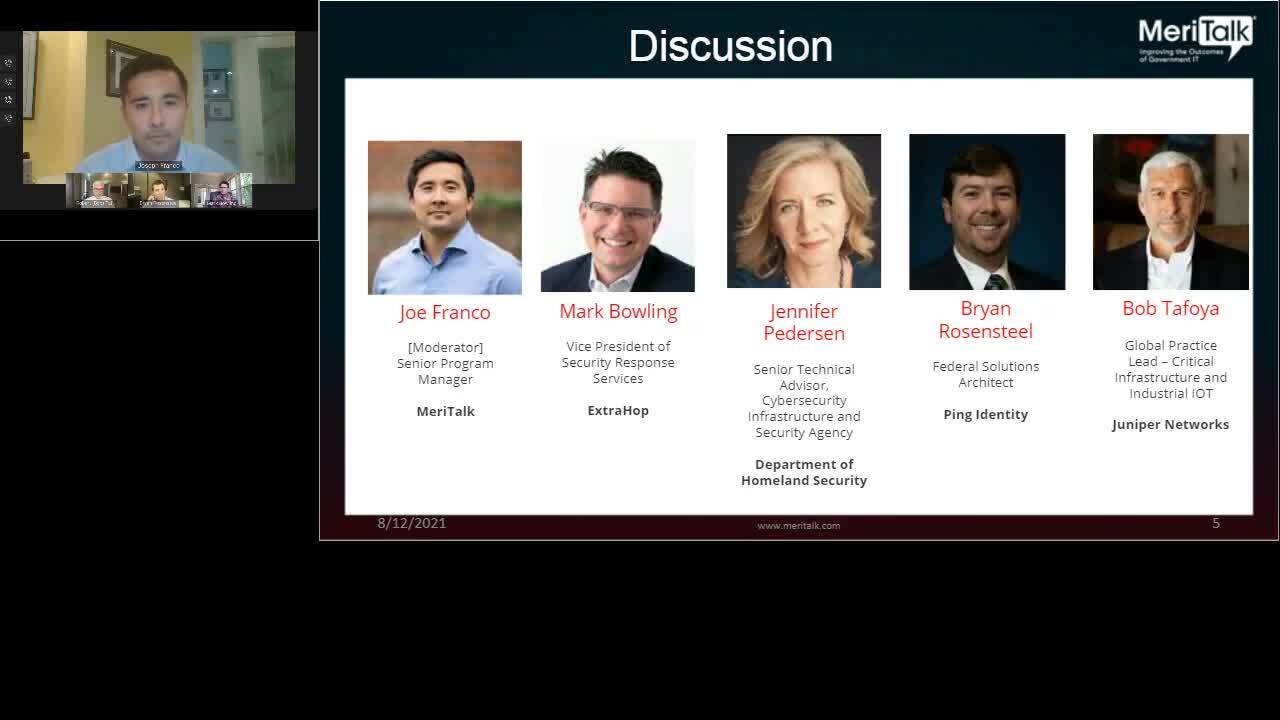
Play video Curbing the Flow of Ransomware: Real or Pipe Dream
Curbing the Flow of Ransomware: Real or Pipe Dream
Industry experts discuss the state of our nation’s cybersecurity, the impact of the Biden administration’s cybersecurity executive order and infrastructure plan, and how government and industry can coordinate to protect critical infrastructure.
1:03:47
-
Play video Ping Identity’s PSD2 & Open Banking Solution Architecture
Ping Identity’s PSD2 & Open Banking Solution Architecture
In this video, we focus on the solution architecture required for banks to not only comply with PSD2 and Open Banking, but also make the customer interactions as simple and seamless as possible.
6:45
-
Play video CCPA: Reasonable Security Requires MFA
CCPA: Reasonable Security Requires MFA
Deepen your understanding of what constitutes “reasonable steps to protect the security of consumers' sensitive information” and how MFA can help you meet information security control expectations under CCPA.
2:03
-
Play video Solving Critical GDPR Challenges
Solving Critical GDPR Challenges
The challenges of GDPR can be solved in part through a comprehensive customer identity and access management (CIAM) solution, while allowing your organization to achieve a better, more cohesive customer experience.
5:57
-
Play video Customer Experience Starts with Data Protection
Customer Experience Starts with Data Protection
Customers expect businesses to protect their data and privacy. Learn how the landscape is changing and how organizations can deliver on these expectations.
12:26