PingOne Verify End User Experience
0:29
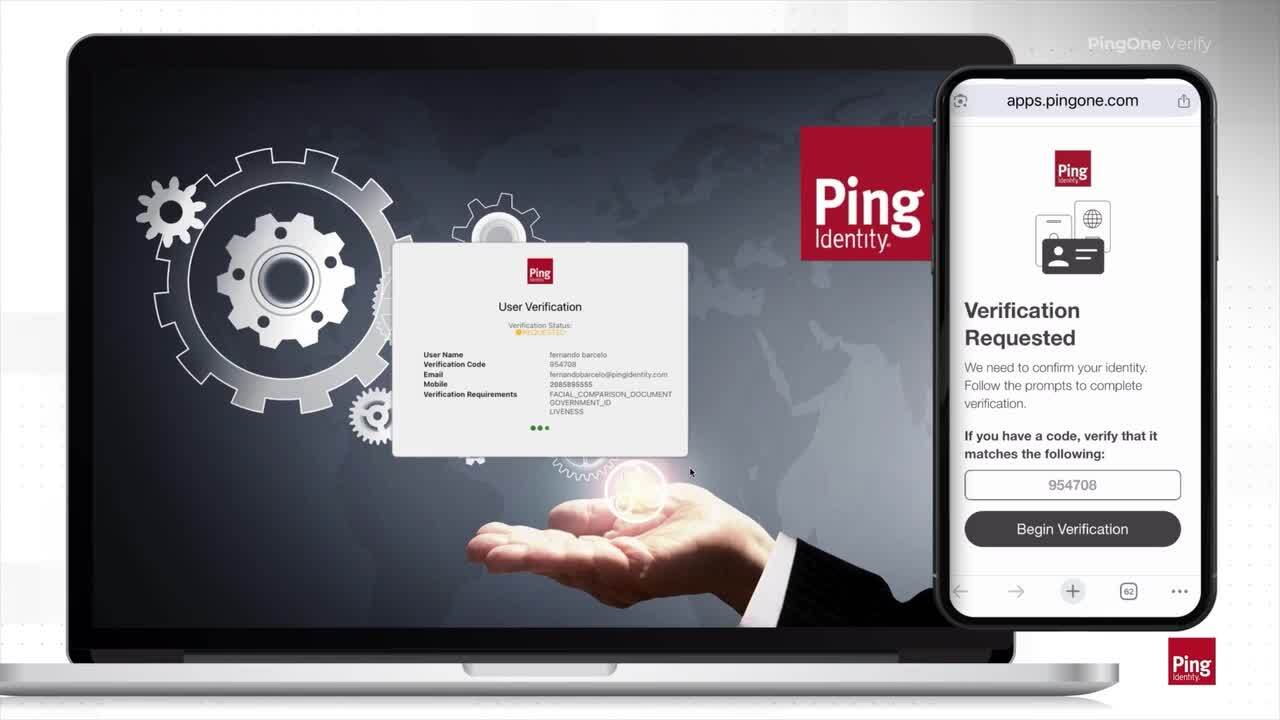
This video shows the full end user experience of doing a full selfie match and document capture with PingOne Verify.
Related Videos
In PingOne Verify
-
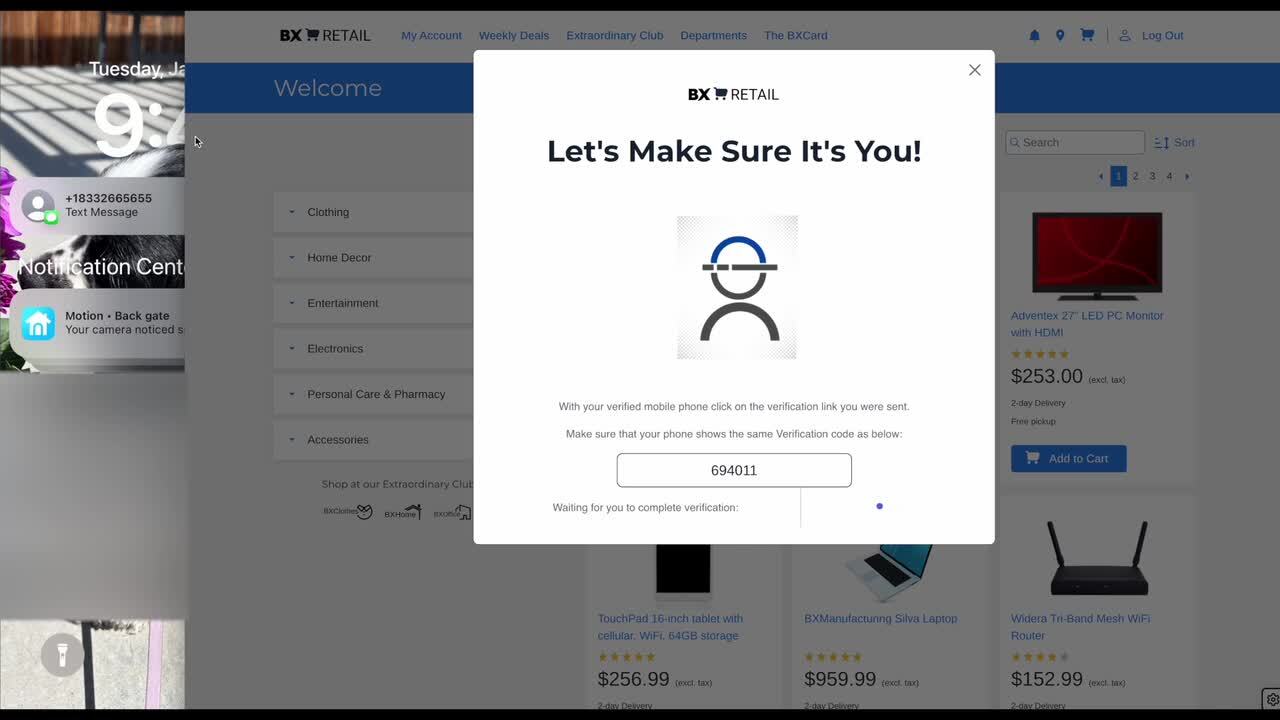
Play video PingOne Verify and PingOne Credentials for Retail Checkout
PingOne Verify and PingOne Credentials for Retail Checkout
The demo video showcases a reimagined retail checkout experience using decentralized credentials and selfie authentication to streamline the process and enhance security, eliminating the need for form filling and traditional login methods.
2:09
-
Play video PingOne Neo Demo Video
PingOne Neo Demo Video
PingOne Neo provides identity verification (proofing), along with digital credential issuance and verification, so organizations can instantly ensure users are who they claim to be.
2:09
-
Play video Demystifying Decentralized Identity with Forrester Research and Ping Identity
Demystifying Decentralized Identity with Forrester Research and Ping Identity
What is decentralized identity? How does it work? What use cases does it solve? All these questions and more and discussed in this fireside chat with Forrester Research VP and principle analyst Andras Czar.
36:06
-
Play video Manage Access for Contractors & Temporary Workers with PingOne Neo
Manage Access for Contractors & Temporary Workers with PingOne Neo
Manage Access for Contractors & Temporary Workers with PingOne Neo
0:38
-
Play video Endless Possibilities with Verifiable Credentials
Endless Possibilities with Verifiable Credentials
Deliver a better user experience with PingOne Neo. With verifiable credentials from Neo, you can verify a persons identity, then issue a digital verifiable credential that will reduce fraud, improve security, and eliminate friction.
1:15
-
Play video Stop Helpdesk Attacks before they Start with PingOne Verify
Stop Helpdesk Attacks before they Start with PingOne Verify
Social engineering attacks on helpdesks are growing. See how PingOne Verify stops them with fast, secure ID confirmation using AI, biometrics, and real-time monitoring.
2:27