Look Beyond OAuth to Secure Digital Experiences
45:39
Description
Related Videos
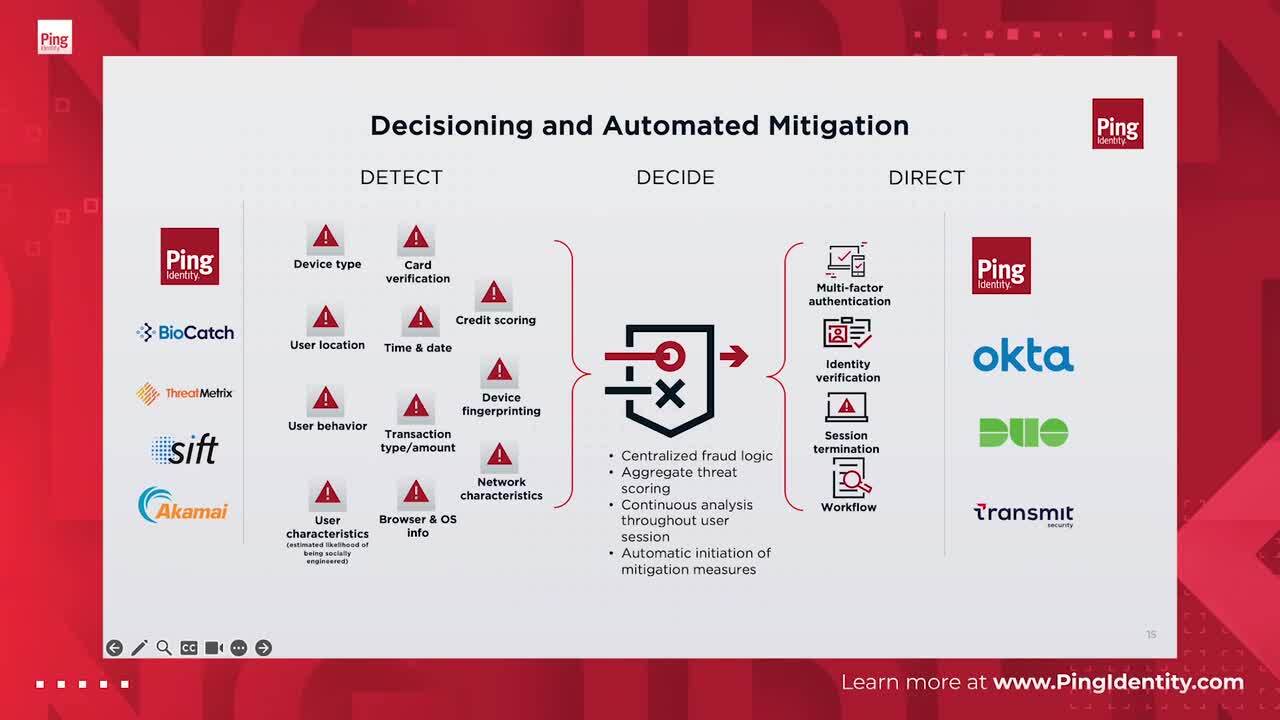
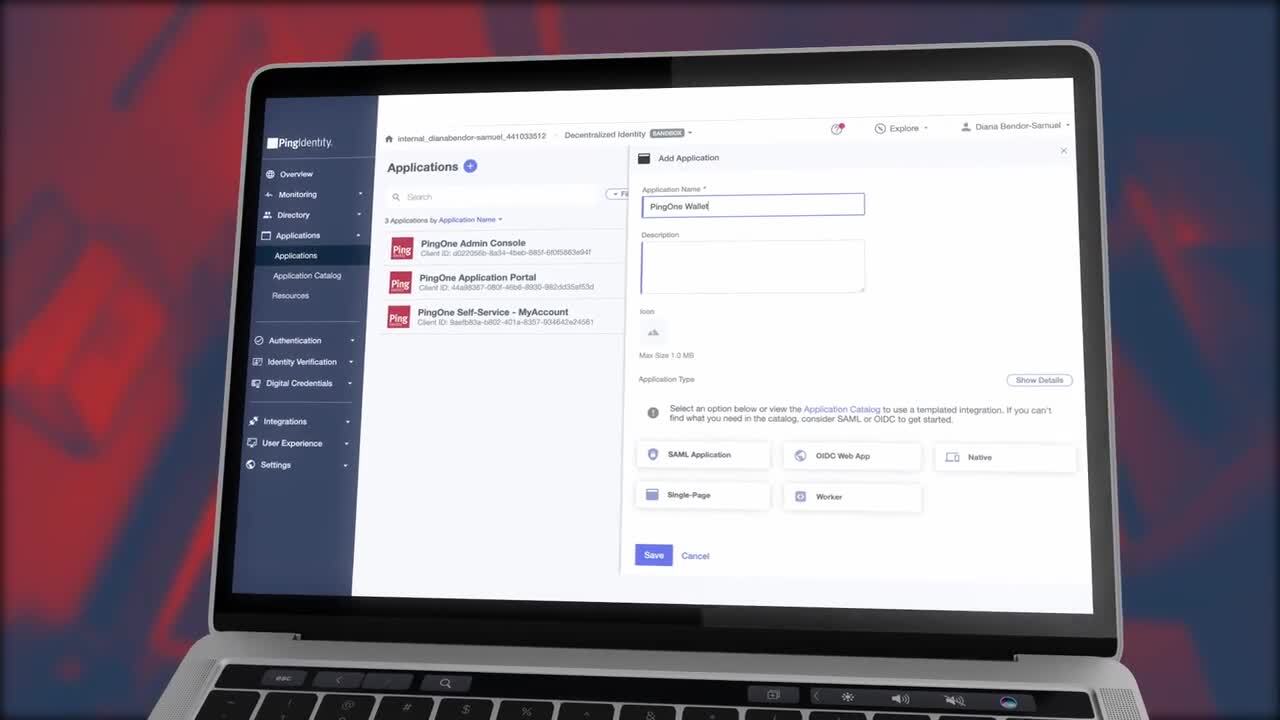
Learn how to use dynamic authorization to go beyond identity and OAuth, leverage real-time context and centralized policy that controls application interactions. To illustrate, we'll take a look at real-world examples of authorization policies.
View More
View Less