Ping Identity Digital Experiences
1:09
Related Videos
In IAM Fundamentals
-
Play video Identity Defined Security with the Ping Identity Platform
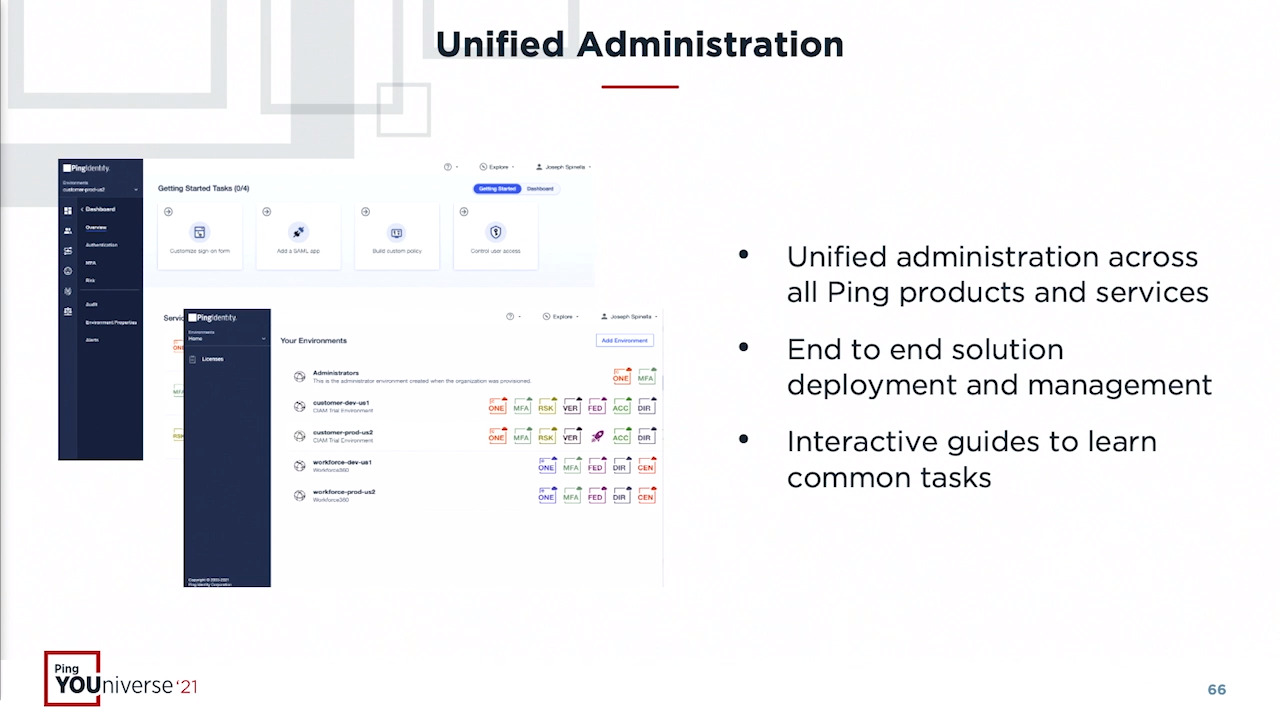
Identity Defined Security with the Ping Identity Platform
As the digital enterprise continues to give users unprecedented access to applications and data, it is imperative they move to dynamic and continuous authentication and authorization with data access governance and privacy management.
5:09
-
Play video Governmental Digital Transformation
Governmental Digital Transformation
Richard Bird, Chief Customer Information Officer at Ping Identity speaks about government prioritization of new Digital Identity initiatives.
2:53
-
Play video The Journey to Identity in the Cloud
The Journey to Identity in the Cloud
Deploying Identity to the cloud can allow your enterprise to reduce infrastructure maintenance costs and enhance your business agility. But moving to the cloud won't happen overnight. Learn how you can migrate your identity solutions to the cloud.
17:13
-
Play video Visualizing PKCE - The Attack
Visualizing PKCE - The Attack
Here's a short scenario to help visualize the attack that sparked the need for PKCE. Gain a deeper understanding of why PKCE is needed by watching this video.
1:41
-
Play video Identity Defined Customer Engagement with the Ping Identity Platform
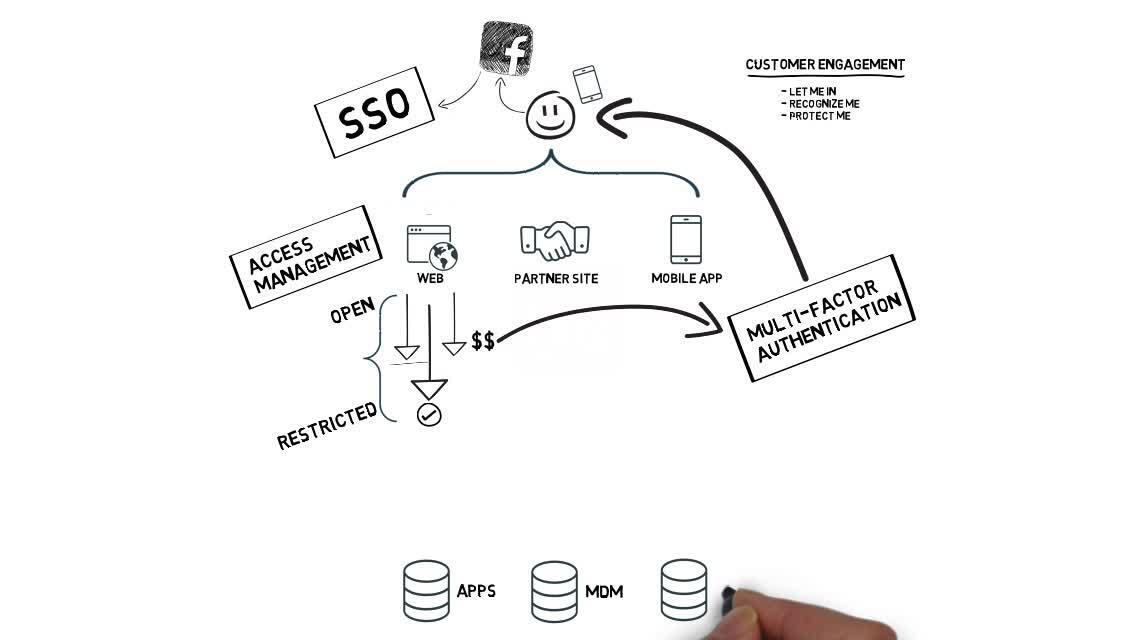
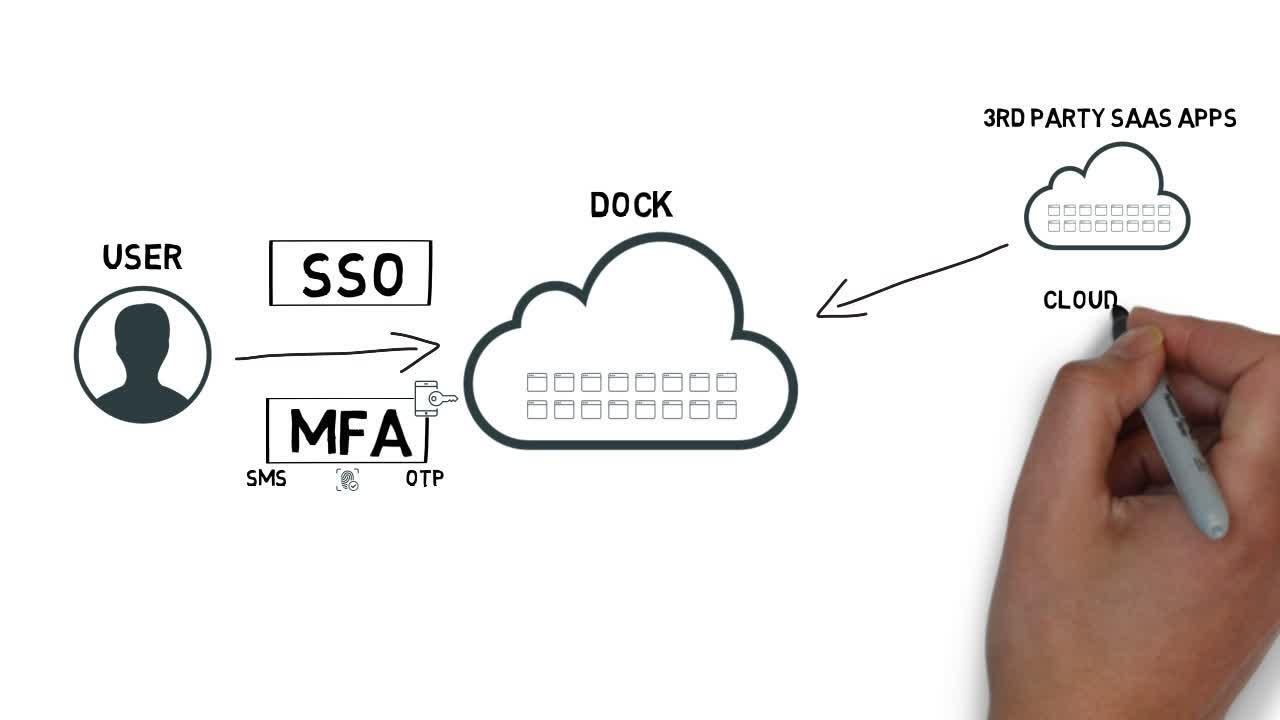
Identity Defined Customer Engagement with the Ping Identity Platform
Enterprises must meet requirements to ensure secure, seamless access across engagement channels.
4:58
-
Play video Security and Agility Can Coexist in the Enterprise
Security and Agility Can Coexist in the Enterprise
Security and agility can be opposing forces in enterprise IT. Improving security alone can slow organizations down, while becoming more agile may increase an enterprise’s vulnerability to attack.
5:13